Data's Last Line of Defense: The Intrinsic Resilience of Storage
Trends
The risks associated with a lack of resilience continue to grow as we move to the AI era and begin to aggregate massive amounts of data. Consequently, enterprises are embracing both data resilience and network resilience as key parts of their protection systems
In 2023, AI foundation models, and ChatGPT in particular, gave rise to a new wave of AI technology development around the world. After being trained by foundation models, AI can make valuable inferences from the massive amounts of aggregated data. Data is the foundation of AI and also the core asset of enterprises. Data resilience is of paramount importance. Splunk's report The State of Security 2023 Is Resilient found that 66% of organizations had been victims of malicious attacks and more than 52% of them had experienced data leakage.
The ever-changing data resilience landscape has driven countries and regions to enact and revise laws and regulations in order to better address data resilience and privacy protection. In 2021, Singapore updated its original data protection legislative framework and released their Personal Data Protection Regulations 2021. In fact, the EU's Network and Information Systems Directive, the US's Federal Trade Commission Act, and Australia's Privacy Act have all been updated to include regulations on data resilience.
Data resilience has become a core indicator of an enterprise or country's competitiveness.
Storage devices are an indispensable part of the data lifecycle, from generation and collection, to transmission, use, and destruction. They typically come with near-data protection and near-media control capabilities, acting both as a home for data and also a safe. As such, they play a critical role in data resilience protection, backup and recovery, and secure destruction.Figure 1: The defense in depth (DiD) model for data resilience
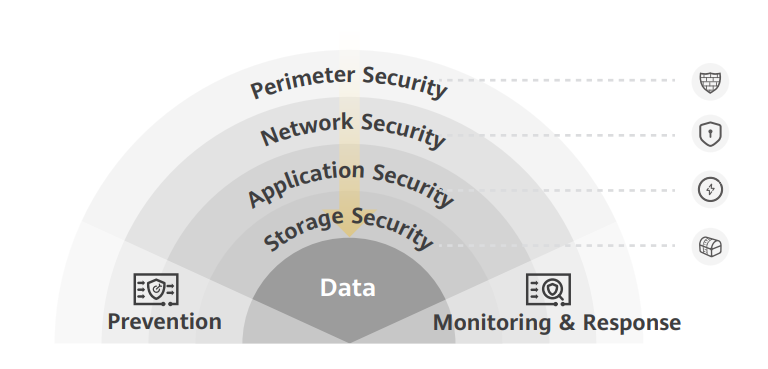
When it came to data resilience in the past, enterprises often prioritized security gateways and application-layer security software. Conversely, they tended to overlook storage and its key role in safeguarding data. It would be comparable to a jewelry store hiring guards and reinforcing their doors and windows, only to leave priceless jewels unprotected on a table inside. Therefore, it is necessary to prioritize storage to ensure data resilience.
The intrinsic resilience of storage builds the last line of defense for data resilience
The intrinsic resilience of storage is built upon an inherently resilient architecture. It has been designed to enhance both storage device resilience and data resilience.
Figure 2: The defense in depth (DiD) model for data resilience

Storage hardware resilience
A root key that functions similarly to an ID card is implanted on the hardware chip, so that each program in the system is authenticated before running, thereby ensuring that the system remains resilient and trustworthy.
Storage software resilience
Storage device resilience can be improved by building security R&D capabilities in compliance with applicable laws and regulations. Selecting high-value open-source software and using standard open-source software facilitate the reliable lifecycle maintenance of all software. Active community feedback and collaborative maintenance ensure the compliant and secure use of software.
Data encryption
Data encryption can be implemented at different layers, such as application software, databases, and storage systems. Application-layer encryption requires a lot of service reconstruction, and database encryption highly compromises performance. Storage devices can use self-encrypting drives (SEDs) to encrypt data, without affecting production services. This encryption method has the best cost-benefit trade-off.
Data ransomware protection
- First, the production storage detects and intercepts ransomware by identifying abnormal reads/writes and calculating information entropy.
- Second, the write once read many (WORM) and secure snapshot features of production storage protect data from unauthorized deletion or being tampered with.
- Third, the ransomware protection storage solution supports rapid recovery using local backups, and this prevents data loss.
- Fourth, an offline data copy is retained in the air-gapped isolation zone, which shields access against ransomware attacks.
Data DR and backup
Data backup: Periodically copying important data to other storage systems in different backup locations ensures that this data can be recovered up to a specific point in time. Backup capabilities can be improved based on service requirements to make the backup system compatible with new core ecosystems such as big data and data warehouses. Full backups of critical data defend against threats caused by human error, hardware faults, and ransomware.
DR: In scenarios without DR, self-built data centers can be used to implement dual DR for data and services so that the DR system can take over production data and services at any time. In scenarios which include existing DR systems, active/standby DR setup can be changed to active-active setup based on service continuity requirements. This ensures zero loss of critical data and defends against a series of threats such as natural disasters, power failures, and computer viruses.
Secure destruction of data
The data on storage devices can be permanently deleted so that it cannot be recovered, and this prevents sensitive data leakage during the resale or discarding of storage devices.

Suggestions
Include storage resilience capabilities in enterprise construction plans when working on network resilience protection projects
Storage has a natural advantage when it comes to resilience as it is deeply connected to the data itself. It can further provide unique data resilience capabilities, such as isolation and recovery, after network interception. Enterprise resilience teams mainly consist of network teams at present. These teams enact strict resilience policies by deploying network resilience devices like firewalls and blocking high-risk ports. In contrast, storage teams tend to focus more on the operations of normal storage resilience services and the planning and development of new storage resilience service technologies.
It is recommended that enterprises add storage resilience capabilities to the resilience system construction projects.
Enhance the software and hardware resilience capabilities of storage devices to improve their overall protection capabilities
Storage devices have to be able to defend against attacks at the underlying storage system layer. By focusing on the structure and design of storage systems and enhancing the resilience capabilities of hardware and software, enterprises can enjoy higher resilience for data and assets thanks to the protection and recovery capabilities of the storage.
Prioritize the deployment of data resilience capabilities such as encryption and ransomware protection for storage devices
Storage devices leverage their advantageous connection to the data and support data-related intrinsic resilience features, which are deployed with optimal reliability, performance, and cost. Data can be encrypted using SEDs to comply with industry requirements and compromise less performance with lower service reconstruction costs. To cope with ransomware attacks, an E2E ransomware protection system must be established to ensure that data can be accurately detected, the system can quickly respond to ransomware attacks, and data can be recovered in a timely manner. In addition, DR resilience must be enhanced, and DR compatibilities with new core ecosystems must be improved on the basis of full DR for mission-critical services and full data backups.
Learn more about Huawei Data Storage and subscribe to this blog to get notifications of all the latest posts.
Disclaimer: Any views and/or opinions expressed in this post by individual authors or contributors are their personal views and/or opinions and do not necessarily reflect the views and/or opinions of Huawei Technologies.
Leave a Comment